Safe Airports
Explore integrated technology designed to ensure airport safety ranging from initial detection to final response across your zones
The Motorola Safety Reimagined Platform for Airports from Flower City Communications & Security
The Intersection Of Technology And Transportation
Today’s airports serve as critical infrastructure around the world. Every day, millions of travelers, workers and pallets of cargo travel in and out of your doors. Your promise — ensure the timely arrival and departure of flights while maintaining a streamlined and enjoyable experience for travelers, shippers and your airport’s businesses. But delivering on this promise is only achievable with a foundation of safety. Everything starts with safety. It’s the center that holds airport operations together.
The Motorola Solutions Safety Reimagined Platform unifies voice, video, data, and analytics technologies on one platform. With Safety Reimagined you can increase security, improve safety, reduce costs, boost efficiency, and improve communications across staff, teams, and locations. These solutions are designed with our customers’ needs at their core; helping Flower City Communications & Security deliver on our promise of creating a safer world.

Safety Reimagined – The Next Generation of Smart Technologies
Improve Safety and Operations on One Platform
Leveraging Motorola’s Safety Reimagined Platform allows your day-to-day operations and emergency situations to be more manageable and measurable for predictable outcomes and optimizations.
Select a use case below and explore
THE SAFETY REIMAGINED INTEGRATED TECHNOLOGY ECOSYSTEM can make a difference in an airport safety situation
Restricted area access
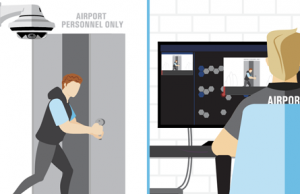
Door alarm triggered. Alert sent to security operations when door opened to restricted area with no code or card swipe directly on the device of their choice and to the command center.

Situational intelligence gathered. Nearby cameras are automatically populated and the closest security resource is determined.

Notification communicated. After the initial alert, intruder image and location sent to nearby security teams in the field to verify identification and authorized access.

Incident managed and reported. Security incident is logged with pre-populated fields and relevant data allowing for further training and analysis.
Airfield breach

Large areas monitored with less. A camera recognizes an individual scaling fence to an airfield and automatically alerts appropriate teams on device of their choice and in the command center.

Appearance tracked. Situational awareness maintained as intruder’s appearance is automatically tracked across multiple cameras on the airfield.

Resources dispatched. Hiding place of intruder is determined and shared across security teams to apprehend intruder.

First response dispatched. Local police directly informed with video for immediate response and incident logged with pre-populated and additional data.
Sterile area breach

Target individual identified. A report of a breach is communicated to airport operations from a security checkpoint.

Appearance tracked. Using an appearance based search, the individual is automatically tracked across all airport cameras in seconds.

Notification communicated. Nearby security teams are mobilized and real time location and image information is shared from airport operations.

Incident managed and supported. Security intercepts individual for proper screening and incident is logged with associated data.
Elevated temperature detection

Elevated temperature detected. A thermal camera at an airport security checkpoint detects a passenger with an indication of elevated body temperature and alerts the security operations center.

Temperature alert verified. The security operations center acknowledges the alert and identifies the passenger with an indication of elevated body temperature.

Resources dispatched. Agents at the security checkpoint are notified of the passenger and a medical professional is dispatched to the checkpoint.

Situation resolved. The passenger is discreetly isolated and a medical screening is conducted and an incident report is automatically logged.
Learn How Safety Reimagined Can Help Your Operations
Safety Reimagined Voice, Video, Data, And Coordination Solutions from Flower City Communications & Security
Improve Safety And Security with a Coordinated Solution
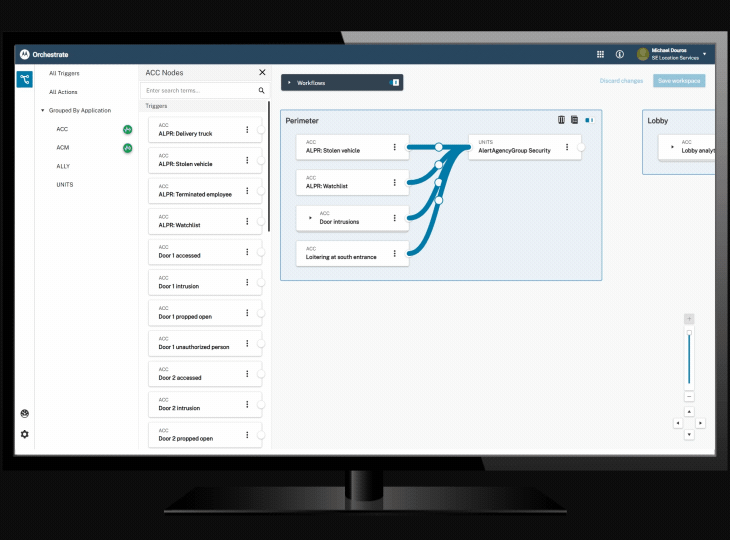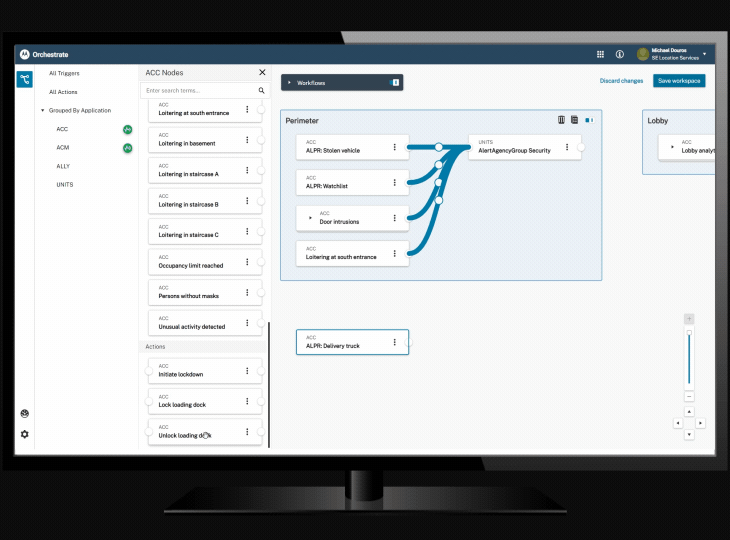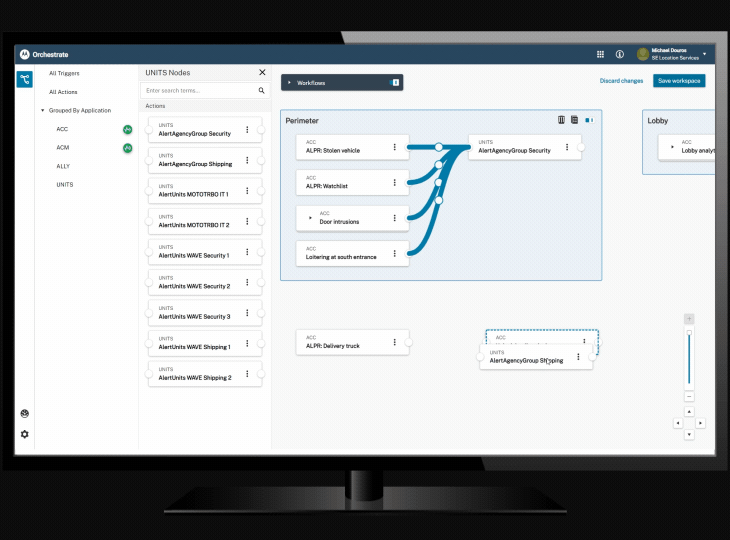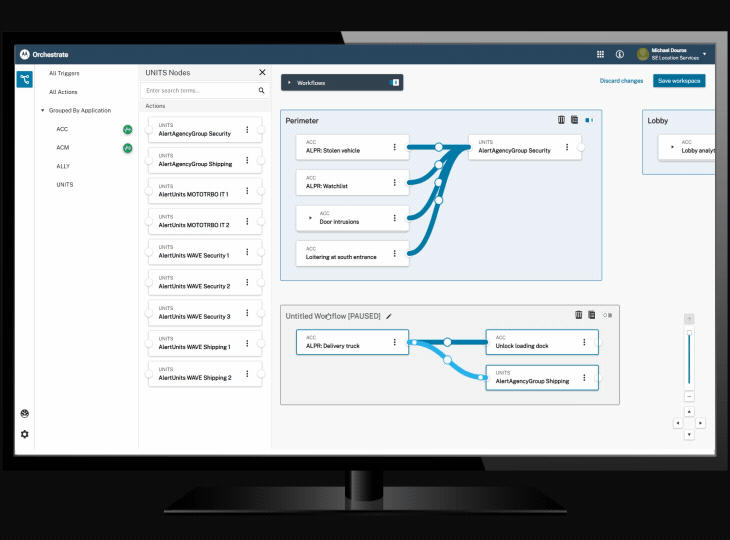
Orchestrate workflow automation tool